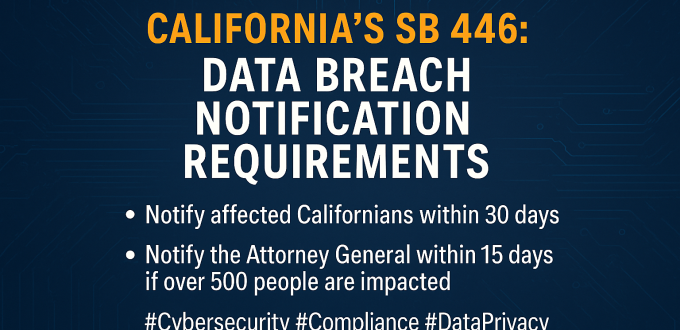
California’s SB 446: What Every Business Needs to Know About New Data Breach Notification Rules Starting January 1, 2026, California’s SB 446 introduces stricter timelines for data breach notifications, replacing the old “without unreasonable delay” standard with firm deadlines. If your organization handles personal data of California residents, this law affects you. Key Requirements Exceptions Why This […]
You are browsing archives for
Category: General IT News
We provide you the important tech, cyber news, and important cyber events. Cyber-security threats and vulnerabilities are threats.
The Salesloft Drift Breach: A Case Study in SaaS Risk, Vendor Transparency, and Cyber Resilience
The Salesloft Drift Breach: A Case Study in SaaS Risk, Vendor Transparency, and Cyber Resilience LinkedIn Article US Service Center September 6, 2025 by Andre Leroux September 6, 2025 In the age of AI-driven automation and cloud-based integrations, the recent breach involving Salesloft’s Drift chatbot has become a stark reminder of the hidden risks lurking […]
When Your Code Supply Chain Becomes a Threat: Lessons from the Recent JavaScript Package Breach
🚨 When Your Code Supply Chain Becomes a Threat: Lessons from the Recent JavaScript Package Breach LinkedIn Article US Service Center September 8, 2025 By Andre Leroux | CEO | Risk Mitigation & Security Advocate This week, the cybersecurity world was shaken by a targeted attack on the open-source ecosystem. At least 18 widely-used JavaScript […]
Microsoft Patch Tuesday – September 2025: What Security Leaders Need to Know
🚨 Microsoft Patch Tuesday – September 2025: What Security Leaders Need to Know LinkedIn Article US Service Center September 9, 2025 by Andre Leroux – CEO | Security Strategist | Risk Mitigation Advocate Microsoft has released security updates addressing over 80 vulnerabilities across its Windows platforms. While this month’s patch bundle contains no known zero-day […]
What is Microsoft Co-Pilot?
Microsoft Copilot: A Smarter Way to Work What is Microsoft Copilot? Microsoft Copilot is a suite of AI-powered assistants integrated into Microsoft products. It began as Bing Chat and has grown into a powerful tool embedded in Word, Excel, Outlook, Teams, and more. What Can Copilot Do? Different Versions of Copilot Is It Free? Yes, […]
How to Recognize and Avoid Tech Support Scams in the Crypto World
As the popularity of cryptocurrency platforms like Coinbase, Binance, Kraken, and others continues to grow, so does the creativity of scammers looking to exploit users. One of the most deceptive and dangerous threats is the tech support scam, where fraudsters impersonate customer service representatives to steal your funds or personal information. What Are Tech Support Scams? Tech support scams […]
The Dangers of Wearable Tech: What You Need to Know
Introduction Wearable technology—smartwatches, fitness trackers, smart glasses, and even smart clothing—has revolutionized how we interact with the digital world. These devices promise convenience, health insights, and seamless connectivity. But beneath the sleek surfaces and glowing screens lies a growing concern: the hidden dangers of wearable tech. This article explores the multifaceted risks associated with wearable […]
5 Ways MSPs Can Strengthen Defenses Against the Evolving Threat of Cyberattacks
How US Service Center Helps Businesses Stay Secure, Compliant, and Confident Introduction Cyberattacks are no longer a matter of “if”—they’re a matter of “when.” From ransomware to phishing to zero-day exploits, today’s threats are more sophisticated, more frequent, and more damaging than ever before. That’s why businesses across the U.S. are turning to Managed Service […]
Why it is important to use a business number versus your personal number
Using a business number instead of your personal cell phone for work has several important benefits: Overall, using a business number helps you maintain a healthier work-life balance, enhances your professional image, and provides better control and security over your business communications.
How to Secure Microsoft 365: Top 10 Best Practices
Microsoft 365 is a powerful suite of tools that can significantly enhance productivity and collaboration. However, securing your Microsoft 365 environment is crucial to protect sensitive data and ensure compliance. Here are ten best practices to help you secure Microsoft 365: 1. Multi-factor Authentication (MFA) Implementing MFA adds an extra layer of security by requiring […]
Trending scams and examples
Knowledge is a powerful defense. Check out these trending scams Trending scams Tech support scams “They needed remote access to remove a virus from my device” How it works: Help protect yourself and your money No matter the reason given, be cautious about granting device access or downloading unfamiliar apps to fix issues with your […]
Developments of Quantum computing
Quantum computing, developed by companies like IBM and Google, promises to solve complex problems in minutes, surpassing today’s supercomputers. Highlights Key Insights of Quantum computing
Safeguarding Your Business
Safeguarding Your Business Safeguarding Your Business is critical to most businesses. Did you know that cybersecurity breaches are projected to cost $10.5 trillion by 2025? Fully automated AI ransomware businesses are being sold on the Dark Web, targeting small businesses. Business owners need to view cybersecurity as an investment in protecting their business and clients, […]
7 critical password rules to practice
There are 7 critical password rules to practice. in your daily lives. For an in-depth understanding of digital security, consider reading the four-volume Digital Identity Guidelines by the National Institute of Standards and Technology (NIST). Although it’s a comprehensive document primarily tailored for Federal agencies requiring highly robust security measures, it also includes a wealth […]
What should you do if you get a pop-up message?
Here’s how to prevent pop-ups from causing harm to your system What never to do when you see a pop-up message It’s crucial to be cautious with pop-up messages, as scammers often use them to trick you into downloading malware or revealing personal information. Your instinct to pause and assess the situation is correct. However, […]
Immutability with Fortified Copies
US Service Center Fortified Copies offer a fresh approach to immutability—protecting servers, workstations, and Microsoft 365 backups, without compromising the ease-of-use US Service Center is known for. Immutability became a hot topic in the data protection space when ransomware groups started targeting backups to thwart victims’ recovery attempts. What is Immutable Data Backup? “Immutable” simply […]
Broad VMware Changes
You may already have heard about the acquisition of VMware by Broadcom. High-level summary? They’ve decided to end the sale of perpetual licenses for VMware products, moving to a subscription model/bundling, and reducing the number of Resellers and Cloud Service Providers. Existing contracts will continue to receive support as outlined in their contractual commitments, but […]
Google and Yahoo are upping their game in 2024
In the on-going battle against spam, Google and Yahoo have announced new standards for 2024 which will help protect their inboxes and reduce spam intrusions. This is great news for legitimate email senders who abide by email best practices. Your business will need to adapt to these new standards or risk non-delivery to the users’ […]
Virtual Kidnapping
Be aware of a New Twist on a Frightening Scam — Virtual Kidnapping. The FBI reports this crime is on the rise. Below are some ways to protect yourself. Don’t Become a Victim The success of any type of virtual kidnapping scheme depends on speed and fear. Criminals know they only have a short time […]
‘Juice Jacking’: The Dangers of Public USB Charging Stations
Juice Jacking and the dangers of Public USB Charging Stations. Are you planning a trip? If so, it’s likely that you’ll bring along your cell phone or another portable device that will need recharging at some point. However, if your battery is low and you plan to use a free USB port charging station, such […]