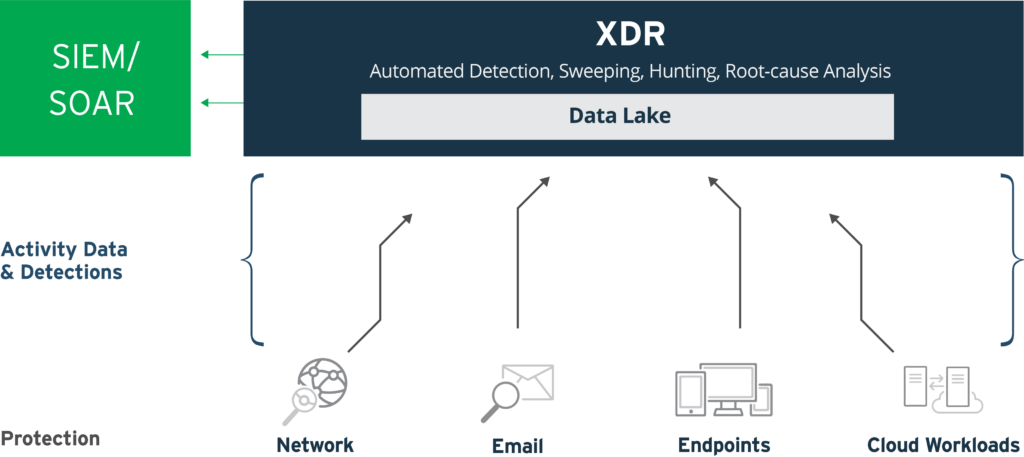
Extended Detection and Response (XDR)
XDR (extended detection and response) collects and automatically correlates data across multiple security layers – email, endpoint, server, cloud workload, and network. This allows for faster detection of threats and improved investigation and response times through security analysis. XDR.
What is the difference between EDR and XDR?
XDR represents the evolution of detection and response beyond the current point-solution, single-vector approach.
Clearly, endpoint detection and response (EDR) has been enormously valuable. However, despite the depth of its capability, EDR is restricted because it can only detect and respond to threats inside managed endpoints. This limits the scope of threats that can be detected as well as the view of who and what is affected. These restrictions ultimately limit response effectiveness within the SOC (Security Operations Center).
Likewise, network traffic analysis (NTA) tools’ purview is limited to the network and monitored network segments. NTA solutions tend to drive a massive number of logs. The correlation between network alerts and other activity data is critical to make sense and drive value from network alerts.
How does XDR work?
Stealthy threats evade detection. They hide between security silos and disconnected solution alerts, propagating as time passes. In the meantime, overwhelmed security analysts try to triage and investigate with narrow, disconnected attack viewpoints.
XDR breaks down these silos using a holistic approach to detection and response. XDR collects and correlates detections and deep activity data across multiple security layers – email, endpoint, server, cloud workloads, and network. Automated analysis of this superset of rich data detects threats faster. As a result, security analysts are equipped to do more and take quicker action through investigations.
What are XDR Security Layers?
When it comes to threat detection, the job of the security operations center (SOC) analyst is to connect the dots from initial infiltration, through lateral movement, to any exfiltration. This process allows for a quicker understanding of the impact and the response actions needed.
The more data sources and security vectors you bring into a single, integrated XDR platform, the greater the correlation opportunities, and the more comprehensive the investigation and response.
For example, today an analyst might use an endpoint detection and response (EDR) tool to get detailed visibility into suspicious activity on managed endpoints – but then have a separate siloed view of network security alerts and traffic analysis. As for the cloud workloads, the analyst likely has limited visibility to identify suspicious activity.
All parts of the environment generate noisy alerts that are likely sent to a security information and event management (SIEM). The analyst can see the alerts, but misses out on a detailed record of all the activity between alerts. Without additional correlation, the analyst will miss important attack details left buried in alerts without context or a way to connect related events.
XDR brings the layers together so security analysts can see the bigger picture and quickly explain what may be happening in the enterprise, including how the user got infected, what the first point of entry was, and what or who else is part of the same attack.
Endpoint
Efficient endpoint activity recording is necessary to analyze how a threat might have arrived, changed, and spread across endpoints. Using XDR, you can sweep for indicators of compromise (IoCs) and hunt for threats based on indicators of attack (IOAs).
Detect: Search for and identify suspicious and dangerous endpoint events
Investigate: What happened on the endpoint? Where did the event come from? How did it propagate across other endpoints?
Respond: Isolate the event, stop processes, delete/restore files
Many organizations may start with endpoint, via EDR tools. While EDR is a good first step, it can miss the beginning and/or end of the attack story. What occurred before it landed on the endpoint? Did it come in through email, and did others receive that same email? What happened after it landed on an endpoint? Was there lateral movement to a server or container? Did it spread to an unmanaged device?
Given that 94% of breaches begin through email,[1] the ability to identify compromised accounts and detect malicious email threats is a critical piece of an organization’s broader threat detection capability.
Detect: Search for and identify email threats, compromised accounts, highly attacked users, and email attack patterns
Investigate: Who enacted the infiltration? Who else received the malicious email?
Respond: Quarantine email, block email senders, reset accounts
Email, as the number one attack vector, should be a priority expansion point for cross-layered detection and response. Email threats often don’t impact endpoints until a user clicks on an attachment or a link embedded in the email. An undetonated threat could be sitting in multiple inboxes undetected. Connecting an endpoint detection with the originating email means you can automatically search inboxes to find who else received the malicious email and if the malicious attachment or URL is also in other users’ mailboxes. You can then subsequently quarantine the emails and remove the threat to prevent any additional spread and damage.
Network
Network analytics is a great way to find targeted attacks as they spread laterally or communicate with command and control (C&C) servers. Network analytics can help filter the events from the noise and reduce blind spots, such as the internet of things (IoT) and unmanaged devices.
Detect: Search for and identify anomalous behavior as threats spread
Investigate: How does a threat communicate? How does it move across the organization?
Respond: Outline the scope of the attack
Network logs provide a comprehensive source of data to help you understand the scope of an attack, but without correlating those logs with other security alerts, it’s hard to get the context you need to assess what’s related and important. For this reason, network and endpoint create a powerful combination. By correlating the data, something that might have seemed benign at just the endpoint layer, such as suspicious PowerShell activity, becomes a high priority alert when it is considered alongside associated C&C communication with a server.
Servers and cloud workloads
Much like endpoints, this involves efficient activity recording to analyze how a threat might have arrived and spread across servers and cloud workloads. You can sweep for IoCs and hunt based on IoAs.
Detect: Search for and identify threats specifically targeting servers, cloud workloads, and containers
Investigate: What happened within the workload? How did it propagate?
Respond: Isolate server, stop processes
Organizations may employ EDR tools for servers and cloud workloads, but may sacrifice effectiveness in doing so. EDR alone is not equipped to address new cloud models nor provide the needed type of data and visibility. As with any vector, correlating information from server environments can validate suspicious activity as malicious – such as servers that communicate with an IP address in a country they’ve never communicated with before – by linking it with activity data from other layers, be it endpoint and/or network.
Superior detection
Leverage a full portfolio of advanced detection techniques against an ever-growing variety of threats and targeted attacks. By integrating endpoint protection and EDR in a single agent, we offer a comprehensive detection and response solution with automation and remediation capabilities.
Root cause analysis and impact assessment
Get complete visibility into the attack vector, see the spread and extent of the impact of advanced threats. Incident response staff can quickly perform impact assessments, determine the root cause of the detection, and take proactive measures to remediate and update security.
Layering in global threat intelligence provides threat investigators with clarity, assistance, and a comprehensive database of threat information.
With our EDR, endpoint analysis can be done in context of other security layers, empowering SOC and security analysts with a single source to run a root cause analysis, look at the execution profile of an attack (including associated MITRE ATT&CK TTPs), and identify the scope of impact across assets.
How XDR Can Help Your Organization?
“By year-end 2027, XDR will be used by up to 40% of end-user organizations.” according to the November 2021 Gartner article.
Extended detection and response (XDR) integrates data from any source to stop modern cyber-attacks. By boosting SecOps efficiency and consolidating siloed products, XDR is gaining momentum as a leading security and risk trend.
[1] Verizon 2019 Data Breach Investigations Report