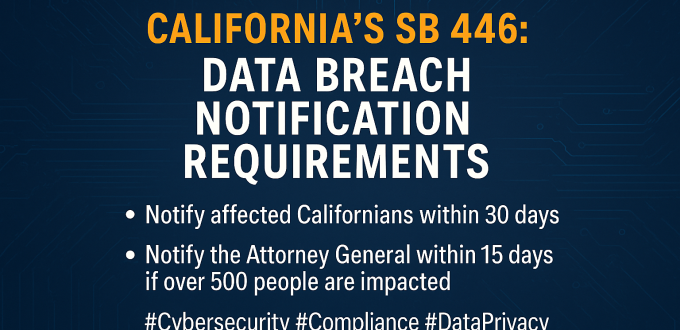
California’s SB 446: What Every Business Needs to Know About New Data Breach Notification Rules Starting January 1, 2026, California’s SB 446 introduces stricter timelines for data breach notifications, replacing the old “without unreasonable delay” standard with firm deadlines. If your organization handles personal data of California residents, this law affects you. Key Requirements Exceptions Why This […]
Technology News & Information
Understanding DMARC: Protecting Your Email from Scammers
Stop Email Spoofing: How DMARC Protects Your Business Have you ever received an email that looked like it came from a trusted company—but it was actually a scam? That’s called email spoofing, and it’s one of the most common ways cybercriminals trick people into giving up sensitive information. At US Service Center, we specialize in […]
The Salesloft Drift Breach: A Case Study in SaaS Risk, Vendor Transparency, and Cyber Resilience
The Salesloft Drift Breach: A Case Study in SaaS Risk, Vendor Transparency, and Cyber Resilience LinkedIn Article US Service Center September 6, 2025 by Andre Leroux September 6, 2025 In the age of AI-driven automation and cloud-based integrations, the recent breach involving Salesloft’s Drift chatbot has become a stark reminder of the hidden risks lurking […]
When Your Code Supply Chain Becomes a Threat: Lessons from the Recent JavaScript Package Breach
🚨 When Your Code Supply Chain Becomes a Threat: Lessons from the Recent JavaScript Package Breach LinkedIn Article US Service Center September 8, 2025 By Andre Leroux | CEO | Risk Mitigation & Security Advocate This week, the cybersecurity world was shaken by a targeted attack on the open-source ecosystem. At least 18 widely-used JavaScript […]
Microsoft Patch Tuesday – September 2025: What Security Leaders Need to Know
🚨 Microsoft Patch Tuesday – September 2025: What Security Leaders Need to Know LinkedIn Article US Service Center September 9, 2025 by Andre Leroux – CEO | Security Strategist | Risk Mitigation Advocate Microsoft has released security updates addressing over 80 vulnerabilities across its Windows platforms. While this month’s patch bundle contains no known zero-day […]
HIPAA Compliance in Real Life: Services and Tools Small Practices Need
HIPAA Compliance in Real Life: Services and Tools Small Practices Need 1. Secure Electronic Health Records (EHR) System 2. Encrypted Email and Messaging 3. Secure Telehealth Platform 4. Business Associate Agreements (BAAs) 5. Cybersecurity Tools 6. Staff Training and Awareness 7. Risk Assessment and Compliance Audits 8. Secure Cloud Storage and Backup 9. Physical Security […]
What Happens If There’s a Breach? The Hidden Cost for Small Practices
The hidden cost of a HIPAA breach For small healthcare providers, a HIPAA breach can be far more than a regulatory issue—it can be a business-altering event. While large institutions may weather the storm with legal teams and crisis management plans, smaller practices often face the consequences more directly and personally. 1. Loss of Patient […]
What is Microsoft Co-Pilot?
Microsoft Copilot: A Smarter Way to Work What is Microsoft Copilot? Microsoft Copilot is a suite of AI-powered assistants integrated into Microsoft products. It began as Bing Chat and has grown into a powerful tool embedded in Word, Excel, Outlook, Teams, and more. What Can Copilot Do? Different Versions of Copilot Is It Free? Yes, […]
Microsoft Authenticator Embraces a Passwordless Future
Microsoft Authenticator Drops Passwords: Ushering in a New Era of Digital Security Published: July 2, 2025 🔐 The End of Passwords? Microsoft Thinks So In a landmark update, Microsoft has officially removed support for traditional passwords in its widely used Microsoft Authenticator app. This move is not just a product update—it’s a bold statement about the future […]
FBI Warns: Millions of Home Devices Hijacked by BADBOX 2.0 Botnet
The FBI has released a high-priority public alert warning that millions of home internet-connected devices are being compromised by a powerful botnet known as BADBOX 2.0. This threat targets everyday smart devices, turning them into tools for cybercrime without users even realizing it. How Are Devices Being Compromised? Cybercriminals are exploiting vulnerabilities in common Internet of […]
What the Kettering Health Ransomware Attack Means for Your Business—and How We’re Protecting You
On May 20, 2025, Kettering Health, a major healthcare provider in Ohio, experienced a devastating ransomware attack that disrupted operations across 14 hospitals and 120+ outpatient facilities. The attackers, known as the Interlock ransomware group, stole and leaked nearly 1 terabyte of sensitive data, including patient records, payroll files, and even police security documents. This […]
How Loneliness Can Lead to Scam Vulnerability: Understanding the Emotional and Psychological Triggers Behind Online Fraud
In today’s hyperconnected world, it’s ironic that loneliness is on the rise. While technology offers endless ways to stay in touch, many people—especially older adults—find themselves increasingly isolated. This emotional gap has become a fertile hunting ground for cybercriminals. According to insights from FightCybercrime.org, loneliness is not just a mental health concern—it’s a significant risk […]
How to Recognize and Avoid Tech Support Scams in the Crypto World
As the popularity of cryptocurrency platforms like Coinbase, Binance, Kraken, and others continues to grow, so does the creativity of scammers looking to exploit users. One of the most deceptive and dangerous threats is the tech support scam, where fraudsters impersonate customer service representatives to steal your funds or personal information. What Are Tech Support Scams? Tech support scams […]
The Dangers of Wearable Tech: What You Need to Know
Introduction Wearable technology—smartwatches, fitness trackers, smart glasses, and even smart clothing—has revolutionized how we interact with the digital world. These devices promise convenience, health insights, and seamless connectivity. But beneath the sleek surfaces and glowing screens lies a growing concern: the hidden dangers of wearable tech. This article explores the multifaceted risks associated with wearable […]
5 Ways MSPs Can Strengthen Defenses Against the Evolving Threat of Cyberattacks
How US Service Center Helps Businesses Stay Secure, Compliant, and Confident Introduction Cyberattacks are no longer a matter of “if”—they’re a matter of “when.” From ransomware to phishing to zero-day exploits, today’s threats are more sophisticated, more frequent, and more damaging than ever before. That’s why businesses across the U.S. are turning to Managed Service […]
Smishing, Vishing, and Spear Phishing: Common Criminal Tactics
Cybercriminals frequently use smishing, vishing, and spear phishing to lure victims onto secondary messaging platforms. Once there, they may deploy malware or share malicious links that lead to fake websites designed to steal login credentials such as usernames and passwords. How to Identify Suspicious Messages Use the following tips to recognize and avoid fraudulent communications: […]
Rebooting your phone daily is your best defense against zero-click attacks – here’s why
In an age where smartphones are central to our personal and professional lives, cybersecurity threats have evolved to become more sophisticated and stealthy. Among the most insidious of these are zero-click attacks—a form of cyberattack that requires no user interaction to compromise a device. While antivirus software and security patches are essential, one surprisingly simple […]
Why it is important to use a business number versus your personal number
Using a business number instead of your personal cell phone for work has several important benefits: Overall, using a business number helps you maintain a healthier work-life balance, enhances your professional image, and provides better control and security over your business communications.
How to Secure Microsoft 365: Top 10 Best Practices
Microsoft 365 is a powerful suite of tools that can significantly enhance productivity and collaboration. However, securing your Microsoft 365 environment is crucial to protect sensitive data and ensure compliance. Here are ten best practices to help you secure Microsoft 365: 1. Multi-factor Authentication (MFA) Implementing MFA adds an extra layer of security by requiring […]
Trending scams and examples
Knowledge is a powerful defense. Check out these trending scams Trending scams Tech support scams “They needed remote access to remove a virus from my device” How it works: Help protect yourself and your money No matter the reason given, be cautious about granting device access or downloading unfamiliar apps to fix issues with your […]