The vast majority (80%) of ransomware attacks can be traced back to common configuration errors in software and devices, according to Microsoft. The tech giant’s latest Cyber Signals report focuses on the ransomware as a service (RaaS) model, which it claims has democratized the ability to launch attacks to groups “without sophistication or advanced skills.’” Configuration Errors Blamed for vulnerabilities.
Among Microsoft’s recommendations for mitigating the ransomware threat are:
- Build credential hygiene: Develop a logical network segmentation based on privileges that can be implemented alongside network segmentation to limit lateral movement.
- Audit credential exposure: Auditing credential exposure is critical in preventing ransomware attacks and cybercrime in general. IT security teams and SOCs can work together to reduce administrative privileges and understand the level at which their credentials are exposed.
- Reduce the attack surface: Establish attack surface reduction rules to prevent common attack techniques used in ransomware attacks. In observed attacks from several ransomware associated activity groups, organizations with clearly defined rules have been able to mitigate attacks in their initial stages while preventing hands on keyboard activity.
- Harden internet facing assets: Consider deleting duplicative or unused apps to eliminate risky, unused services. Be mindful of where you permit remote helpdesk apps like TeamViewer. These are notoriously targeted by threat actors to gain express access to laptops.
- Address Security Blind Spots: Like smoke alarms, security products must be installed in the correct spaces and tested frequently. Verify that security tools are operating in their most secure configuration, and that no part of a network is unprotected.
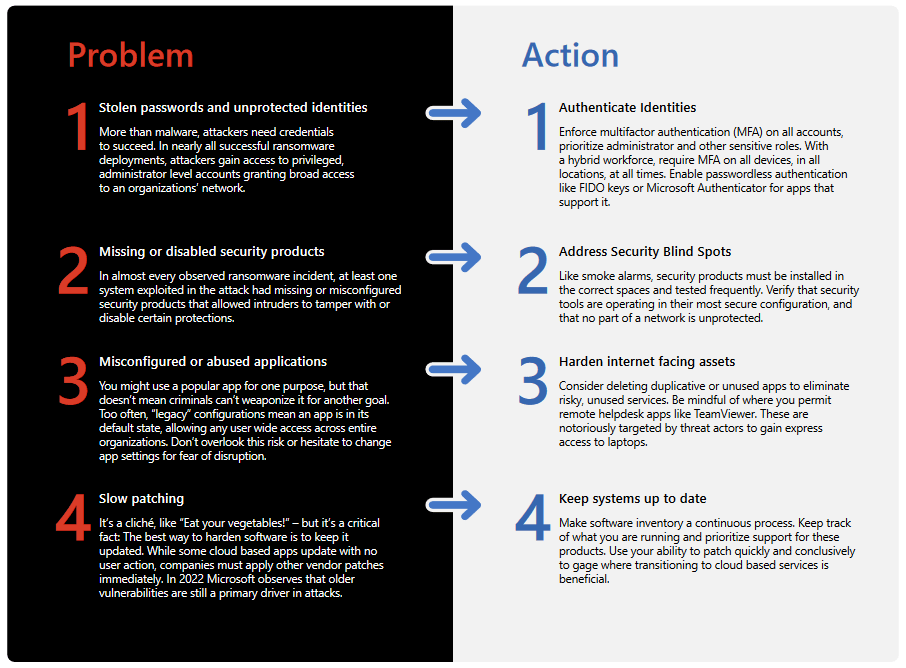
Problems – Configuration Errors Blamed
- Stolen passwords and unprotected identities
More than malware, attackers need credentials to succeed. In nearly all successful ransomware deployments, attackers gain access to privileged, administrator-level accounts granting broad access to an organizations’ network. - Missing or disabled security products
In almost every observed ransomware incident, at least one system exploited in the attack had missing or misconfigured security products that allowed intruders to tamper with or disable certain protections. - Misconfigured or abused applications
You might use a popular app for one purpose, but that doesn’t mean criminals can’t weaponize it for another goal. Too often, “legacy” configurations mean an app is in its default state, allowing any user wide access across entire organizations. Don’t overlook this risk or hesitate to change app settings for fear of disruption. - Slow patching
It’s a cliché, like “Eat your vegetables!” – but it’s a critical fact: The best way to harden software is to keep it updated. While some cloud-based apps update with no user action, companies must apply other vendor patches immediately. In 2022 Microsoft observes that older vulnerabilities are still a primary driver in attacks.
Actions
- Authenticate identities
Enforce multifactor authentication (MA) on all accounts, prioritize administrator and other sensitive roles. With a hybrid workforce, require MFA on all devices, in all locations, at all times. Enable passwordless authentication like FIDO keys or Microsoft Authenticator for apps that support it. - Address security blind spots
Like smoke alarms, security products must be installed in the correct spaces and tested frequently. Verify that security tools are operating in their most secure configuration, and that no part of a network is unprotected. - Harden internet facing assets
Consider deleting duplicative or unused apps to eliminate risky, unused services. Be mindful of where you permit remote helpdesk apps like TeamViewer. These are notoriously targeted by threat actors to gain express access to laptops. - Keep systems up to date
Make software inventory a continuous process. Keep track of what you are running and prioritize support for these products. Use your ability to patch quickly and conclusively to gage where transitioning to cloud-based services is beneficial.
Understanding the interconnected nature of identities and trust relationships in modern technology ecosystems, they target telecommunications, technology, IT services, and support companies to leverage access from one organization to gain entry into partner or supplier networks. Extortion only attacks demonstrate that network defenders must look beyond end-stage ransomware and keep a close eye on data exfiltration and lateral movement.
If a threat actor is planning to extort an organization to keep their data private, a ransomware payload is the least significant and least valuable part of the attack strategy. Ultimately, it’s an operator’s choice what they choose to deploy, and ransomware is not always the big-ticket payout every threat actor is after.
While ransomware or double extortion can seem an inevitable outcome from an attack by a sophisticated attacker, ransomware is an avoidable disaster. Reliance on security weaknesses by the attackers means that investments in cyberhygiene go a long way.
Microsoft’s unique visibility gives us a lens into threat actor activity. Rather than rely on forum posts or chat leaks, our team of security experts study new ransomware tactics and develop threat intelligence that informs our security solutions.
Integrated threat protection across devices, identities, apps, email, data and the cloud help us identify attacks that would have been labeled as multiple actors, when they’re in fact a single set of cybercriminals. Our Digital Crimes Unit composed of technical, legal, and business experts continues to work with law enforcement to disrupt cybercrime.
Recommendations:
- Harden the cloud: As attackers move towards cloud resources, it’s important to secure these resources and identities as well as on-premises accounts. Security teams should focus on hardening security identity infrastructure, enforcing multifactor authentication (MFA) on all accounts, and treating cloud admins/tenant admins with the same level of security and credential hygiene as domain admins.
- Prevent initial access: Prevent code execution by managing macros and scripts, and enabling Attack Surface Reduction Rules.
- Close security blind spots: Organizations should verify that their security tools are running in optimum configuration and perform regular network scans to ensure a security product protects all systems.
Microsoft has in-depth recommendations at https://aka.ms/ransomware-as-a-service and also at this web seminar.
Source: Microsoft, Extortion Economics, Ransomware’s new business model, August 22, 2022

